3 Types of Cyber Attacks Your Manufacturing Business Needs to Anticipate
 Did you know that manufacturing is one of the most susceptible industries to cyber attacks?
Did you know that manufacturing is one of the most susceptible industries to cyber attacks?
While manufacturers agree this is an area of concern, most have been slow to adopt any sort of cybersecurity assessment or disaster plan. That is according to our 2019 State of Northeast Ohio Manufacturing Report, where a small 12% of manufacturers reported undergoing a formal assessment and only 5% reported that they plan to invest in cybersecurity in 2019.
Anticipating cyber attacks allows manufacturers to proactively defend intellectual property, saving thousands of dollars in financial loss. However, it’s uncommon for manufacturers to have the infrastructure in place to prevent such attacks—let alone trained security on staff.
To protect your manufacturing business against cyber attacks, I've outlined the following common attacks to be aware of with and tips for preventing, detecting, and responding to an attack.
1. Phishing
Phishing is an alarming trend for employers everywhere. Just ask Schletter Inc., a global solar panel manufacturer and distributor in North Carolina.
In 2016, an employee responded to a cybercriminal posing as the company’s CEO. The result was the disclosure of the personal information of more than 200 employees. The employee fell victim to an increasingly common cyber attack known as phishing, a fraudulent attempt to lure confidential information by disguising oneself as a legitimate source.
In this example, Schletter Inc. failed to educate its employees on basic cybersecurity measures like data disclosure, resulting in a lawsuit. And as a result, the company is now responsible for sensitive information falling into the wrong hands.
Here's an example phishing email:
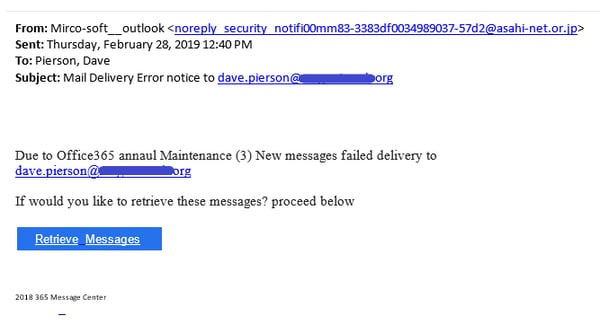
To thwart these types of attacks, have your employees exercise caution when handling sensitive information. Common warning signs of phishing include:
- Attachments with dangerous file types
- Immediate demands or requests
- Lucrative offers with attention-grabbing statements
- Misspelled hyperlinks of known websites
- Unusual email sender(s)
- Threats
By implementing training sessions on data disclosure, you can protect your business and its employees from the dangers of phishing. That way, employees will know how to recognize and respond to phishing, lessening the likelihood of such attacks.
2. Supply Chain Attacks
Complex supply chains operate more efficiently when data is shared between manufacturers and their suppliers and vendors. However, this also increases your chances of an attack if unauthorized users get access to your network.
According to CSO, “A supply chain attack occurs when someone infiltrates your system through an outside partner or provider with access to your systems and data.”
Here are common signs your network has been hacked by a third party:
- Faulty usernames and passwords upon logging into software systems
- Odd redirects to unknown sites
- Pop-up ads
- Ransomware messages
- Software freezes or crashes
To prevent stolen data, manufacturers must vet business partners carefully and conduct regular security audits to ensure they’re keeping any shared data safe.
3. Malware
While the benefits of adopting 4.0 technologies are well known, there’s still a large portion of manufacturers lagging behind.
Nearly 75% of manufacturers operate legacy systems that aren’t built to account for today’s security threats. And when computer systems are outdated, the chance of experiencing a cyber attack dramatically increases.
A legacy system can be the gateway for malware to spread throughout a network and disrupt production. Malware is a term used to describe malicious code that blocks access to key components of a network to gain access to sensitive information.
To protect against malware, manufacturers can take the following steps:
- File encryption
- Implement two-step verification
- Install antivirus software on computers
- Mandate encryption of data transmissions
- Update operating systems, browsers and plugins
- Safeguard usernames and passwords
- Secure Internet connections with firewalls
Step Up Your Cybersecurity Game
MAGNET’s cybersecurity experts offer formal cybersecurity threat assessments that help you identify vulnerabilities to keep your company safe from hackers. Contact us to prepare your company for the future.


.png?width=1024&name=MAG_Visual-CTA_Contact_Cyber_V1%20(1).png)


